Install Unbound DNS Resolver For PI Hole
This is an easy install which will help secure your network and also speed browsing up when using Pi Hole
So what is Unbound and why Use it ?
Unbound is a validating, recursive, caching DNS resolver. It is designed to be fast and lean and incorporates modern features based on open standards. Late 2019, Unbound has been rigorously audited, which means that the code base is more resilient than ever.
The advantages:
- No third party other than your ISP has access to your entire DNS history. Your ISP sees the DNS traffic, but even if you hid the traffic from the ISP, they can quickly figure out where you are browsing based on the clear text IP’s you request. So, instead of having to trust your ISP and an upstream DNS provider, you only need to trust the ISP.
- No filtering – the nameservers reply with the correct answers and there is no potential for a different IP that may be provided by an ISP DNS server or an upstream DNS service that has their own filtering.
- Speed – for the initial lookups, it takes a few hundred msec. Once the unbound cache is primed, it has a number of techniques to maximize answers from cache, including pre-fetching information before it expires. In practice, it is quite fast.
- Control – when you run your own resolver, you can control to a large extent how it operates. There are a number of configuration options available in unbound.
Install Unbound
SSh into the PI Hole server or open the Terminal
sudo apt install unbound -y
Should onlt take a few seconds, next we have to add a config
sudo nano -w /etc/unbound/unbound.conf.d/pi-hole.conf
Copy all of the text below and paste it into the editor
server: # If no logfile is specified, syslog is used # logfile: "/var/log/unbound/unbound.log" verbosity: 0 interface: 127.0.0.1 port: 5335 do-ip4: yes do-udp: yes do-tcp: yes # May be set to yes if you have IPv6 connectivity do-ip6: no # You want to leave this to no unless you have *native* IPv6. With 6to4 and # Terredo tunnels your web browser should favor IPv4 for the same reasons prefer-ip6: no # Use this only when you downloaded the list of primary root servers! # If you use the default dns-root-data package, unbound will find it automatically #root-hints: "/var/lib/unbound/root.hints" # Trust glue only if it is within the server's authority harden-glue: yes # Require DNSSEC data for trust-anchored zones, if such data is absent, the zone becomes BOGUS harden-dnssec-stripped: yes # Don't use Capitalization randomization as it known to cause DNSSEC issues sometimes # see https://discourse.pi-hole.net/t/unbound-stubby-or-dnscrypt-proxy/9378 for further details use-caps-for-id: no # Reduce EDNS reassembly buffer size. # IP fragmentation is unreliable on the Internet today, and can cause # transmission failures when large DNS messages are sent via UDP. Even # when fragmentation does work, it may not be secure; it is theoretically # possible to spoof parts of a fragmented DNS message, without easy # detection at the receiving end. Recently, there was an excellent study # >>> Defragmenting DNS - Determining the optimal maximum UDP response size for DNS <<< # by Axel Koolhaas, and Tjeerd Slokker (https://indico.dns-oarc.net/event/36/contributions/776/) # in collaboration with NLnet Labs explored DNS using real world data from the # the RIPE Atlas probes and the researchers suggested different values for # IPv4 and IPv6 and in different scenarios. They advise that servers should # be configured to limit DNS messages sent over UDP to a size that will not # trigger fragmentation on typical network links. DNS servers can switch # from UDP to TCP when a DNS response is too big to fit in this limited # buffer size. This value has also been suggested in DNS Flag Day 2020. edns-buffer-size: 1232 # Perform prefetching of close to expired message cache entries # This only applies to domains that have been frequently queried prefetch: yes # One thread should be sufficient, can be increased on beefy machines. In reality for most users running on small networks or on a single machine, it should be unnecessary to seek performance enhancement by increasing num-threads above 1. num-threads: 1 # Ensure kernel buffer is large enough to not lose messages in traffic spikes so-rcvbuf: 1m # Ensure privacy of local IP ranges private-address: 192.168.0.0/16 private-address: 169.254.0.0/16 private-address: 172.16.0.0/12 private-address: 10.0.0.0/8 private-address: fd00::/8 private-address: fe80::/10
When copied use CTRL+X and then CTRL+Y and ENTER to save the config.
Then Restart the Unbound Service
sudo service unbound restart
Then run
sudo service unbound status
That should then let you know that the it is Active (running)
In the unbound config we made we set it to be running on 127.0.0.1 (localhost) and port 5335
So to test that unbound is configured properly use this command
dig machman.co.uk @127.0.0.1 -p 5335
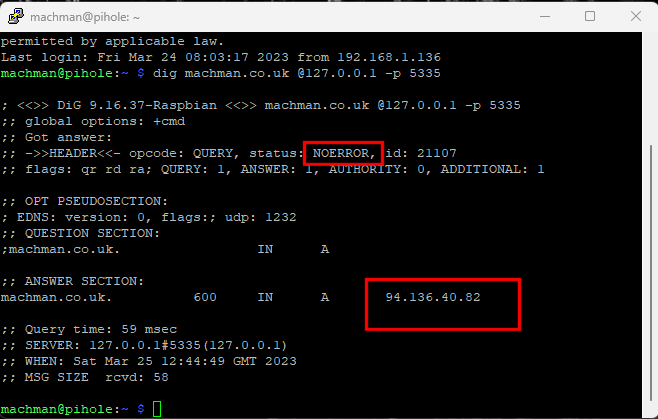
As you can see we have the status NOERROR and we also get an IP for the query
So thats Unbound all Setup and ready to use
We just need to tell Pihole to use it.
Open the PI Hole Admin Page and go to settings and then DNS
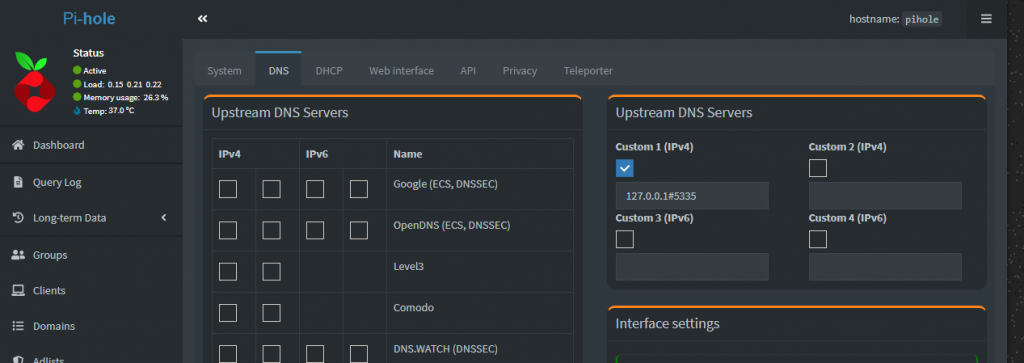
Untick whichever Upstream DNS Servers you had chosen and tick the Custom 1 (IPv4) box and fill with
127.0.0.1#5335
Scroll down the Page and Click Save and thats it done
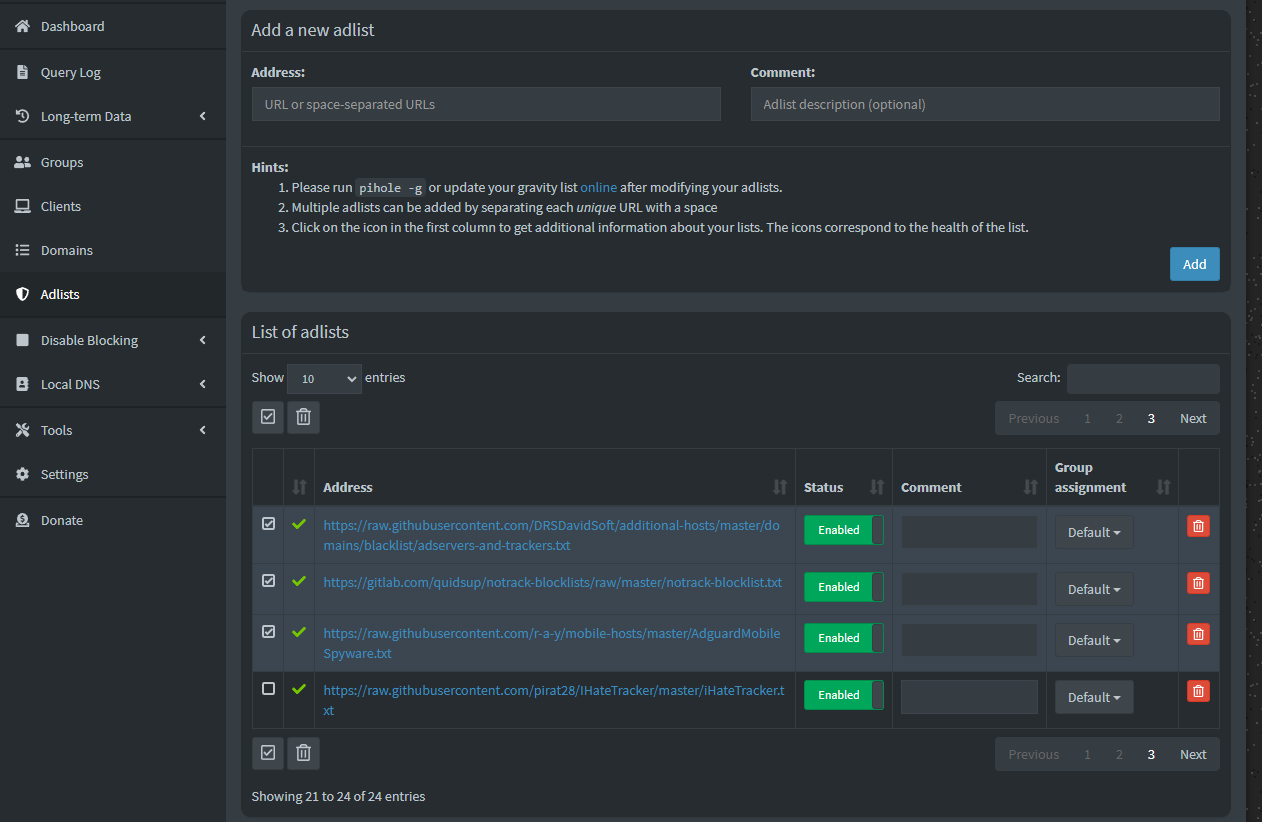
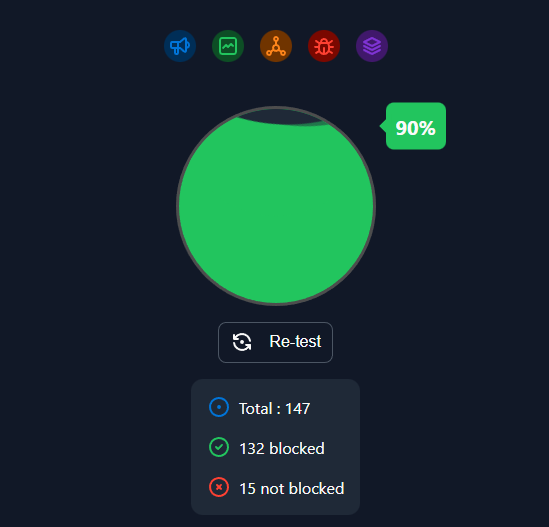
A good test for Ad Blocking is Here
https://d3ward.github.io/toolz/adblock.html

As you can see at the time of writing i block 90% of ads which is pretty good but i am determined to get that to 100% but that requires a bit of tuning.
Addendum
Some have reported that occaisionally Unbound will stop and not serve any DNS Queries
If this is happening do the following from a SSH Session or a terminal
sudo nano /etc/resolvconf.conf
Edit file /etc/resolvconf.conf and comment (#) out the last line which should read:
unbound_conf=/etc/unbound/unbound.conf.d/resolvconf_resolvers.conf
Change to
#unbound_conf=/etc/unbound/unbound.conf.d/resolvconf_resolvers.conf
Delete the unwanted unbound configuration file:
sudo rm /etc/unbound/unbound.conf.d/resolvconf_resolvers.conf
Restart unbound:
sudo service unbound restart
Then it should work as planned